In today’s digital world, authorization is essential for protecting sensitive data and ensuring that only authorized users can access specific resources. Traditional authorization systems can be complex and difficult to manage, especially for large and complex applications. Ory Permissions is a modern permission system that aims to address these challenges by providing a flexible, scalable, and tech-stack agnostic solution.
How to integrate permission checks to your application
This guide will show you how to use Ory Permissions in your project. Whether you’re starting a new project or adding security features to an old one, Ory Permissions can help you control who can do what in your application.
Understand Ory Permissions
By following the design ideas from the Zanzibar paper, Ory Permissions gives some advantages compared to other permission systems:
In Ory Permissions, there are two main ideas: relationships and permissions. These help you control who can do what in your application.
- In Ory Permissions, relationships are pieces of information about things stored in the system. A relationship includes three parts: something (like a file), a description of how it’s related (like “owns”), and another thing (like a user). These relationships show how different parts of your application are connected. For instance, you could create a relationship between a user and a file to indicate that the user is the owner of that file.
- In Ory Permissions, permissions are rules written in a language like TypeScript. These rules are like small programs that decide whether someone can do something based on the connections between things in Ory Permissions. They let you set up who can do what in your app very precisely, matching exactly what your app needs.
- When you mix these rules with the connections between things, you can make detailed plans for who can access what in your app. Ory Permissions lets you make these plans flexible, so they fit any kind of app. This means you can make rules that are as simple or as complicated as you want, while keeping your app safe.
- Ory Permissions also gives you tools to handle these rules and connections in your app. For example, you can organize your stuff into groups using “namespaces,” and there’s a special way to talk to Ory Permissions from your app to set up and change these rules automatically.
Benefits of Ory Permissions
Ory Permissions provides flexible, scalable, and secure access control, seamlessly integrating with any tech stack, simplifying management and ensuring optimal performance.
Flexibility: Ory Permissions is designed to be flexible and adaptable to a wide range of use cases. It supports various authorization models, including role-based access control (RBAC), attribute-based access control (ABAC), and policy-based access control (PBAC). This flexibility allows you to tailor the authorization system to meet the specific needs of your application.
Scalability: Ory Permissions grows with your app. It can handle lots of users, permissions, and stuff without slowing down. This makes it good for both small and big companies.
Tech-Stack Agnostic: Ory Permissions works with any tech setup. It fits with any programming language, framework, or database you’re using. So, you can add it to your system easily, no matter what tech you’re using.
Ease of Use: Ory Permissions is simple to use and control. It has an easy interface for managing who can do what. This makes it easy for both developers and admins to use, even if they’re not experts in permissions.
Security: Ory Permissions is super secure. It follows the best security practices to keep your data safe. Only the right people can access important stuff, keeping everything secure.
How Ory Permissions Works
Ory Permissions consists of two main components:
- Ory Keto Permission Server: The Ory Keto Permission Server is the core of Ory Permissions. It is an open-source authorization server that stores and manages permissions, roles, and policies.
- Ory SDKs: Ory Permissions provides SDKs for various programming languages and frameworks. These SDKs allow you to integrate Ory Permissions into your applications and interact with the Ory Keto Permission Server (available in programming language – dotnet, go, java, python, typescript, ruby and dart)
When a user tries to access a resource in your application, the application first sends a request to the Ory Keto Permission Server. The Ory Keto Permission Server then evaluates the user’s permissions against the relevant policies and determines whether to grant or deny access to the resource.
Keto Concept
- Relationships: – Relationships are the underlying datatype of Ory Permissions. They encode relations between objects, which are the resources that you want to manage to, and subjects, which are the people or things that want to access these resources. A relationship is associated with a namespace where its relation has to be defined and configured.
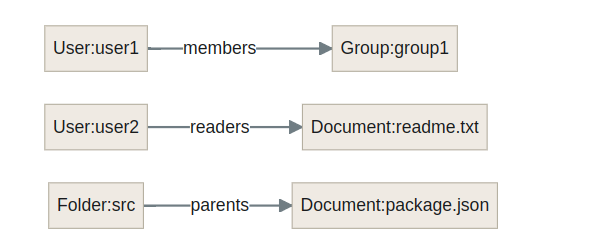
User:user1 is in members of Group: group1
User:user2 is in readers of Document:readme.txt
Folder’s is in parents of Document:package.json
User1 is a member of Group1: This means that User1 belongs to Group1, implying that User1 likely has access to resources or privileges associated with Group1.
User2 is a reader of Document “readme.txt”: This indicates that User2 has permission to read the document named “readme.txt,” suggesting that User2 can view its contents.
Folder is a parent of Document “package. Json”: This signifies that the folder contains the document “package. Json,” implying a hierarchical relationship where the folder houses the document.
https://research.google/pubs/zanzibar-googles-consistent-global- a uthorization-system/
Group: group1#members@User:user1
The graphical representation looks like this: –
- Namespaces: –
In Ory Permissions, namespaces do two main things:
- They help organize things and people.
- They hold rules that decide which connections are checked when permissions are checked.
Each namespace has a bunch of permissions that decide which connections are checked. For instance, when checking if User “Bob” can view a file named “readme.txt” in the “Document” namespace, the system looks up certain connections to make that decision.
is User: bob in viewers of Document:readme.txt
// all viewers can view the document
is User: bob in editors of Document:readme.txt
// all editors can view the document
is User: bob in owners of Document:readme.txt
// all owners can view the document
In the Ory Permission Language, namespaces are like categories and should be named after the singular form of what they describe, like User, Document, Folder, or Access Key. Each name should start with a capital letter, like User or Document.
When naming relationships within a namespace, use plural words that describe how a subject is related to an object. Each relationship should make sense as an English sentence. For example:
Subject belongs to Object’s members.
- Objects: –
Objects are names given to things in an app, like files or items. Apps need to give each thing a unique name, which can be up to 64 characters long.
We suggest using UUIDs for names because they’re unique and secure, but you can also use URLs or other random codes. Objects are considered the same if their names are the same.
For instance, in Ory Permissions, you can use any string as a name for things, but it’s not a good idea to put app data directly in the name. Instead, use UUIDs to link app data with object names. This ensures:
- One main source for data and easy updates.
- You can use any characters for naming (except # and @).
- No limit on data size.
For example, this could be used to set up rules for value ranges. The app knows how UUIDs correspond to certain conditions.
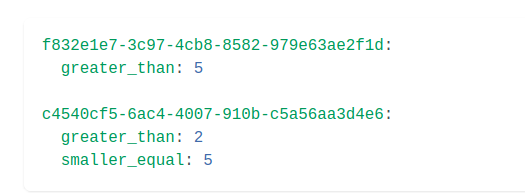
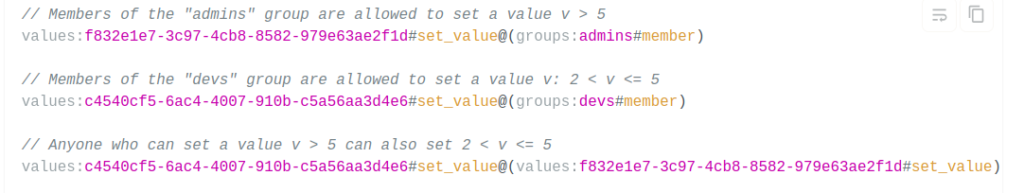
Ory Permissions has the following relationships:
- Subjects: –
In Ory Keto, subjects are a type of data that can refer to specific individuals or groups of individuals. These individuals can be identified by a name chosen by the app, like usernames, or they can be groups of individuals.
Subject IDs:
- These are just names given to individuals, like usernames or unique codes.
- It’s best to use UUIDs because they’re unique and secure, but you can also use URLs or other codes.
- Subjects are considered the same if their names are the same.
Subject sets:
This refers to groups of individuals that have a certain connection to something, like a file or a resource.
They make Ory Permissions very flexible because they allow for indirect connections.
They can be used to set up things like who can access certain files or inherit permissions.
Subject sets can also refer to other subject sets, or they can be empty, meaning they include all subjects related to something.
Subject sets also represent all the in-between connections in a network of relationships.
Basic example:
In a simple case, an app might use usernames or unique IDs to identify individuals.
For example, a user might have a username like “zelatrix” or a unique ID like “480158d4-0031-4412-9453-1bb0cdf76104.”
Think of it like this: subjects are like the characters in a story, and subject sets are like the groups they belong to or the roles they play in the story.