With the surge in cyber threats and privacy issues, implementing a robust Identity and Access Management (IAM) solution is paramount. Beyond security, a dedicated IAM tool is essential for maintaining the separation of concerns between business logic and user management. After assessing numerous open-source options such as Keycloak, Zitadel, and Casdoor, we ultimately chose Ory for its exceptional alignment with our business requirements. Ory’s standout feature is its modular architecture, which segments the entire IAM system into four distinct components. These components can be utilized independently to address specific business needs and can be easily integrated with other systems. In this blog post, we will delve into these key components, the challenges we encountered, and the standout features that set Ory apart.
What is ORY?
ORY is an open-source ecosystem of identity and access management (IAM) tools built with a zero-trust network wrapped around its four components. It is designed to simplify the implementation of secure authentication and authorization in web applications. Developed with scalability, flexibility, and ease of use in mind, ORY provides a comprehensive set of components that cover the entire lifecycle of user identity management.
Key components of Ory
There are four key components of Ory, which can be independently used as per the business requirements.
- Ory Kratos
- Ory Keto
- Ory Oathkeeper
- Ory Hydra
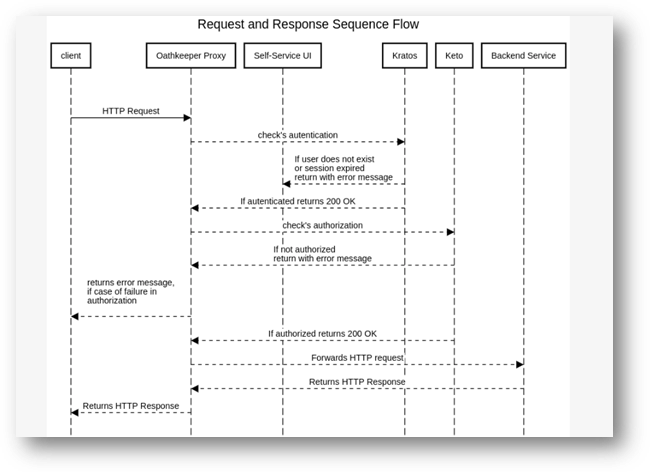
Below is the sequence diagram illustrating the interaction between Ory components and our application. This diagram shows an overview of how these components interact and work together to fulfill authentication and authorization requirements within our architecture.
These are the three major Ory components –
Ory Kratos
Ory Kratos: An Open-Source Identity and User Management System
It is a user authentication and account management system designed to make user profile management in web applications simpler for developers.
Think of it as the gatekeeper that controls who can access your application and manages user accounts behind the scenes.
Key features includes –
Ory Kratos offers a wide range of authentication methods:
- Password: Users authenticate by providing their password, which is the traditional method of authentication.
- OIDC (OpenID Connect): Users authenticate through OIDC by signing in with a social sign-in provider, such as Google or Facebook.
- TOTP (Time-Based One-Time Password): Users authenticate by entering a time-based one-time password generated by an authenticator app or hardware token.
- WebAuthn: Users authenticate through a WebAuthn channel, which supports various methods such as OS-level biometric authentication (e.g., fingerprint or face recognition) or hardware tokens (e.g., YubiKey).
- Lookup Secret: Users authenticate by entering a valid one-time recovery code, which is often used as a backup authentication method for scenarios like account recovery.
Ory Kratos offers a convenient way to customize your signup page fields using a file called Identity Schema.
Now, a question arises about how these fields are directly rendered on your UI (Sign up Pages of Self-service UI). The process is that the fields specified in the Identity Schema. JSON files are parsed directly as form input elements.
By adjusting the Identity Schema!
JSON file, you can easily manage and update the fields displayed on your signup page, making it simpler for users to register and providing you with greater control over the collected information during the signup process.
At the database level, information about users is stored mainly in three columns of the identity table: traits, metadata public, and metadata admin.
Traits are stored as JSON fields, allowing for flexible storage of key-value pairs. You can store a variety of information within traits. However, it’s important to note that as the JSON structure grows larger, the token length may increase. This could potentially lead to an increase in token length, which may have implications for token-based authentication. These fields are typically visible on the settings page of your UI, providing users with access to manage their information.
Metadata Admin: Metadata stored in the metadata admin column is intended for information that should be managed at the admin level, such as user roles. This data is typically not exposed to users through the UI and is managed via admin API endpoints. It provides a way to store sensitive or administrative information securely.
Metadata Public: Similar to metadata admin, metadata stored in the metadata public column can be accessed and updated by users without requiring admin API endpoints. This column is useful for storing non-sensitive user information. (Note: these fields are also not visible on UI, specifically the settings page of self-service UI)
What are Ory Kratos browser flows?
ORY Kratos provides browser-based authentication and account management flows that enable users to register, log in, log out, and manage their accounts through a web interface. These flows are designed for easy integration into web applications.
Here’s an explanation of the browser flows provided by ORY Kratos:
Registration Flow:
- Allows users to create a new account on your application.
- After successful registration, the user is typically redirected to a confirmation page or automatically logged in to the page specified in default return urls.
Login Flow:
- Allows registered users to log in to your application.
- ORY Kratos verifies the credentials and issues a session cookie upon successful authentication.
- The session cookie is used to authenticate subsequent requests to protected endpoints.
Logout Flow:
- They are typically initiated by clicking a “Logout” button or link.
- ORY Kratos invalidates the session cookie associated with the user’s session, effectively logging them out.
- After logging out, users are usually redirected to a logout confirmation page or back to the login page, depending on the flow you have set in config.
Settings Flow:
- Allows users to manage their account settings.
- Users can update their profile information, change their password, and perform other account-related actions.
- Provides a user-friendly interface for managing account details without requiring administrative intervention.
Recovery Flow:
- Provides a way for users to recover access to their account if they forget their password or encounter other login issues.
- Typically, it involves requesting a password reset link via email or other verification methods.
- Users follow the link to reset their password and regain access to their account.
Verification Flow:
- Allows users to verify their email address or phone number after registration.
- Often involves sending a verification code or link to the user’s email or phone number.
- Users follow the link or enter the code to confirm their contact information and complete the verification process.
These flows can be customized and integrated into your web application to provide a seamless and secure user experience.
You can easily customize these flows from the Kratos.yaml file. For example, what are your default return browser URLs, where the browser will redirect the user after the flow is completed?
However, one aspect that we’re still researching is whether users can be redirected to the same page of the UI from which they were logged out. This presents an interesting challenge and requires further investigation. If you have any insights or ideas on how this can be achieved effectively, we welcome your input and collaboration.
Benefits:
- Security: Ory Kratos is built with security in mind and follows cloud architecture best practices. It supports several features to help keep your users’ accounts safe, such as multi-factor authentication (MFA/2FA), account verification, and secure password management.
- Flexibility: Ory Kratos is designed to be flexible and can be adapted to meet the specific needs of your application. You can use the Ory Account Experience available in Ory Network or can setup on premise, and you can use JSON Schema to accommodate different data fields of Self-Service Ui (login UI provided by Ory).
- Ease of use: Ory Kratos is easy to use and deploy. It can be run on any operating system and most processors, and it has no system or library dependencies. You can use the Ory network in the cloud or deploy it on premise.
- Scalability: Ory Kratos can be scaled both horizontally and vertically based on your application needs.
- Support for multiple databases: Ory Kratos supports multiple database integration, including SQLite, PostgreSQL, MySQL, and Cockroach DB.
Ory Oathkeeper
In the world of web development, securing APIs and controlling access to resources is essential for protecting sensitive data and ensuring the integrity of applications. ORY Oathkeeper is a powerful tool designed to simplify API access control and authorization, making it easier for developers to secure their applications. We’ll explore ORY Oathkeeper, its key features, and flows.
What is ORY Oathkeeper?
ORY Oathkeeper is an identity and access proxy (IAP) that acts as a gatekeeper for your APIs, enforcing authentication and authorization policies before allowing access to protected resources. It provides a centralized way to manage access control rules and policies for your APIs, ensuring that only authorized users and applications can interact with them.
Key Features of ORY Oathkeeper:
- API Access Control: Oathkeeper allows you to define access control rules and policies for your APIs, specifying who can access which resources and under what conditions. This helps you enforce security requirements and prevent unauthorized access to sensitive data.
- Authentication: Oathkeeper supports various authentication methods, including OAuth 2.0, OpenID Connect, JSON Web Tokens (JWT), and basic authentication. It verifies the identity of users and applications by connecting to Kratos before granting access to protected APIs.
- Authorization: Once authenticated, the oathkeeper evaluates authorization policies through keto to determine whether the authenticated user or application has the necessary permission to access the requested resource. This helps you enforce fine-grained access control and restrict access to specific endpoints or actions.
- Flexible Configuration: Oathkeeper is highly configurable and supports different deployment supports. You can define access control rules using YAML or JSON configuration files, customize authentication and authorization workflows, and integrate Oathkeeper with other identity providers and authentication services.
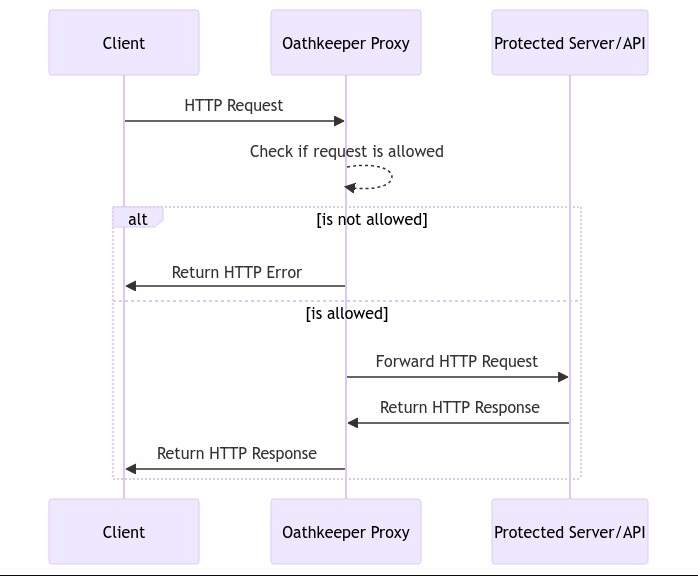
How does the ORY Oathkeeper work?
Request Evaluation Flow
- When a client sends a request to an API protected by Oathkeeper, Oathkeeper intercepts the request before it reaches the API server.
- Oathkeeper evaluates the request against the configured access control rules and policies to determine whether the client is authorized to access the requested resource.
- If the request passes authentication and authorization checks, Oathkeeper forwards the request to the API server for processing.
- If the request fails authentication or authorization checks, Oathkeeper returns an appropriate error response to the client. It supports different error handlers.
- One of the remarkable features of Oathkeeper is mutators, which allow you to configure how the information should be sent to the backend.
- In our current architecture, we leverage mutators to convert user information into a JWT token format, which can be securely transmitted to the backend services.
- Oathkeeper offers a variety of mutators, allowing us to customize the transformation process according to our specific business requirements. You can read more about them at Ory Mutator.
An interesting consideration regarding our architecture is the interaction between Ory Oathkeeper and services utilizing Server-Sent Events (SSE) or WebSocket connections, which rely on continuous connections. It’s important to note that passing requests through Ory Oathkeeper may be better for such scenarios as it can lead to request timeout issues.
While Ory Oathkeeper does allow you to specify a timeout parameter in its configuration, enabling it to handle requests with longer durations, there are practical limitations to how long you can keep these connections open. Continuous connections like Server-Sent Events (SSE) or WebSocket often require longer timeouts to maintain their connectivity, which may not be feasible or efficient within the context of Ory Oathkeeper.
Additionally, we would like to mention Ory actions, which play an essential role in our existing architecture. Ory actions act as triggers that are invoked whenever a specific event occurs within the system. For instance, in our current setup, we utilize a web hook action that is invoked immediately after user registration. This action is designed to verify specific details or perform additional operations in response to the registration flow.
One of the aspects of Ory actions is the ability to define custom web hook actions tailored to our specific requirements. This flexibility empowers us to seamlessly integrate with our existing architecture and extend the functionality of our identity and access management system as needed.
Basic flow diagram of how an incoming request is processed through Oathkeeper
Self-service UI Node
Self Service UI Node is an open-source application designed to manage Kratos browser flows. It is built using NodeJS, Typescript, and handlebars, which handle the UI rendering part of the application.
It uses the Ory SDK, which is written in TypeScript, to handle the processes Kratos browser flow implementation is correct and secure. These include user signup, login, password reset, and account settings changes.
By utilizing the Ory SDK, the application can efficiently manage these user-related operations. Self-Service UI Node application handles basic errors correctly. These include “Not Found” (404), “Resource Not Available” (410), “Access Forbidden” (403), “Internal Server Error” (500), and errors related to user authentication.
Advantages of using Self Service UI Node:
- Ease of Implementation: Using Self Service UI Node makes it easier to implement user login, registration, and account management. It reduces the complexity and potential for errors. Implementing the Ory SDK is task which needs expertise of its own.
- Quick Start: The Self Service UI Node provides pre-built UI pages, which saves development and integration time and allows developers to focus more on the application’s core features.
- Built-in Security: The Self Service UI Node comes with built-in security features. These ensure a secure foundation for your application and reduce the risk of security issues.
- Maintenance: With Self Service UI Node, updates and improvements are handled by the Ory team. This means you benefit from the latest security patches and feature enhancements without the need for manual updates.
Customization Possibilities with Self Service UI Node:
- Customizing the UI: The self-service UI node uses Server-Side Rendering, which can make UI customization a bit complex, especially when div classes overlap. But we can still make changes using Descendant Selectors and CSS hierarchy.
- Adding New Routes: We can introduce new routes in the self-service UI node. These can be used for different purposes, like handling custom errors. We just need to declare the custom route controller and register the handlebar view file to the server.
- Customizing Error Messages: For status codes like 500 & 404, we can alter the error messages directly in the code. This lets us change the title and body of the error message.
Limitations of using Self-service UI Node:
- Customizing Kratos Browser Flow: Altering the functionalities of forms within the Kratos browser flow is complex and not recommended. Changes may disrupt the predefined flow and cause unexpected behavior.
In conclusion, Self Service UI Node offers a robust solution for managing Kratos browser flows, streamlining user authentication processes, and enhancing security. Its ease of implementation, pre-built UI pages, and built-in security features make it a compelling choice for developers. However, while it simplifies many aspects of user management, customizing the Kratos browser flow can be complex and may require careful consideration to avoid disrupting the predefined flow. Despite this limitation, the platform’s maintenance handled by the Ory team ensures ongoing updates and improvements, promising a secure and reliable user experience. We will be discussing more about it, so stay updated with the next chapter of this series.
References: